In these parts, I will show and explain how to configure and use the AVI integration with NSX-T Data Center Distributed Firewall (DFW).
- Prelude : AVI SE in NSX-T Exclusion List
- Part 1 : NSX-T Security Group used as a back-end server pool
- Part 2 : Deploying SEs using NSX-T DHCP & NSX-T DFW
- Part 3 : From Virtual Service into NSX-T DFW
The version of NSX-T I used was 3.1.1 (due to old configurations, I use the Manager Policy for the DFW) and AVI 20.1.5.
When we say AVI Integration with NSX-T, it means that we create an “NSX-T Cloud” from AVI.
Official AVI Documentation related to this topic: https://avinetworks.com/docs/20.1/nsx-t-no-se-in-exclude-list/#creating-dfw-rules
Prelude AVI SE in NSX-T Exclusion List
Before the integration between AVI and NSX-T DFW, we needed to put the SE vms in the NSX-T DFW Exclusion list.
This solution was quite embarrassing. The idea with AVI SEs is to have SE groups working in Active/Active mode.
Using this mode, it’s possible and we often want our SEs to scale out (can be deployed dynamically when needed).
Here for each new SE, we must add them to the exculison list. Otherwise, the SEs can’t reach the AVI Controllers.
I will just explain in this prelude Post how to create a group, put the SE VMs on this group using the the Security Tag (matching criteria of the Security Group) and apply this group to the Exclusion list.
First, we create a new NSX-T Group and we specify the tag criteria we want to use on our SE VMs.
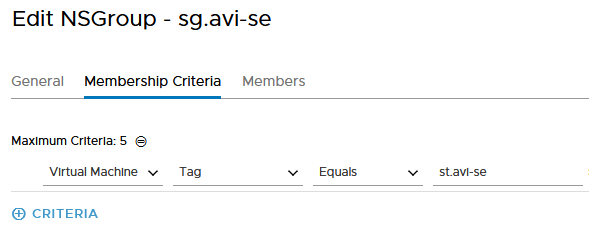
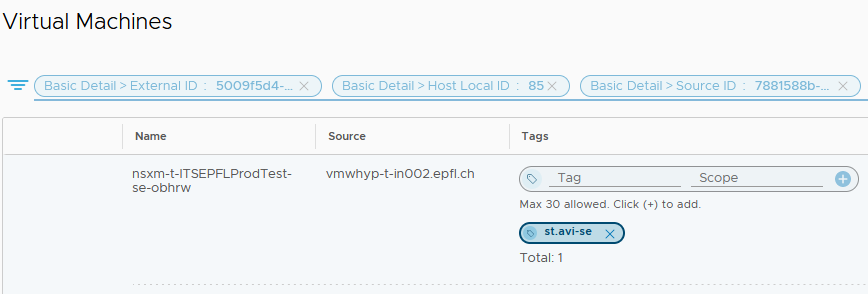
Then we add this Security Tag to all our existing SE VMs and don’t forget the coming ones.
The best would be to add this Security Tag dynamically once the SE VM creation is done.
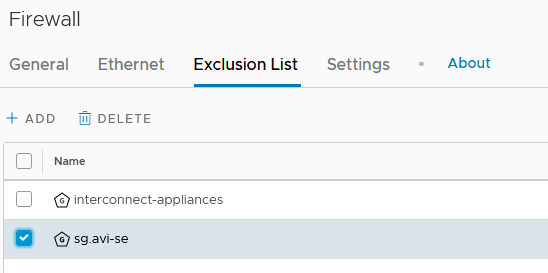
Under the Distributed Firewall Tab, you will find the Exclusion List.
You just have to add your Security Group.
In the following posts, we will see how to integrate AVI Service Engine (SE) and Virtual Service (VS) into our NSX-T DFW in order to remove this group from the Exclusion List and give a real FW security to our components.
