In these two parts, I will show and explain to you how to set UP and configure a connection beetwenn you NSX-T Datacenter on-prem and an SDDC on the cloud.
- Part 1: On-premise
- Part 2: VMware Cloud on AWS
- Part 3: Filtering BGP routes
VMware Cloud on AWS (Cloud side)
Note: In these articles, I assumed people have already some knowledge about NSX-T components and are familiar with the NSX Manager UI, the edges and T0.
For privacy and security purpose, I will hide my on-premise public IP and the VMC public IP.
The version of NSX-T I used was 2.5.1 -> https://docs.vmware.com/en/VMware-NSX-T-Data-Center/2.5.1/rn/VMware-NSX-T-Data-Center-251-Release-Notes.html
I want to warmly thanks my VMware beast colleague Eric Krejci, the VMware NSX-T and VMC teams for their support.
From the VMC side like shown in my schema above, there are two diffenrent sides:
– The compute, where we are going to create our workload networks and VMs.
– The management (SDDC), which contains our mgt appliances and our cloud ESXi hosts.
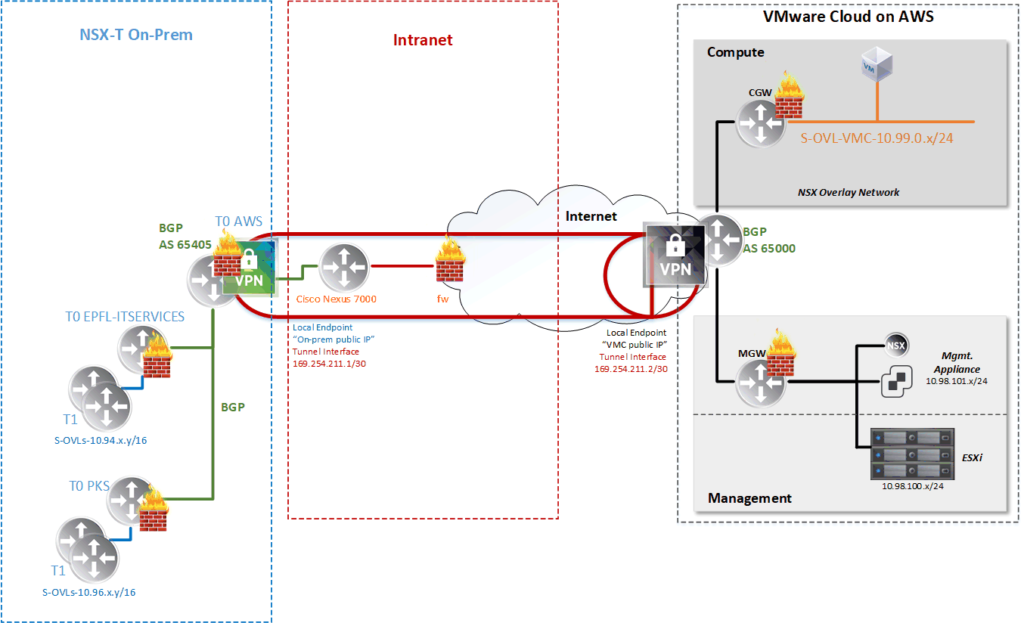
At the creation of our SDDC, we provides a /23 subnet for the Management part, in our case 10.98.100.0/23.
The first /24 is used for the ESXi hosts and the second for the appliances.
Here is the dashboard of our VMC.
IPsec VPN configuration
All the VPN configuration is down under the “Networking & Security”.
It’s easier to configure than the NSX-T part because we don’t have any profiles choose and so on.
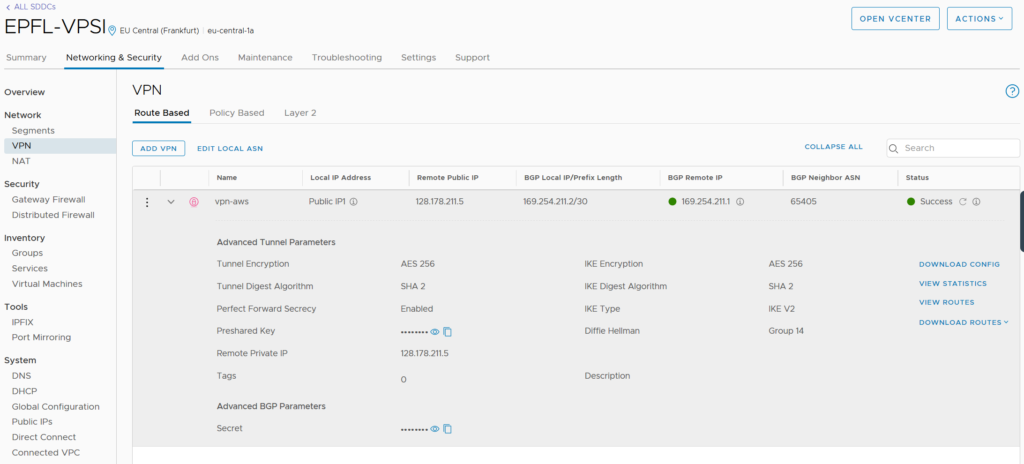
For the BGP configuration we can only set the BGP Remote ASN number and the secret. There is no possibility to configure BFD (Bidirectional Forwarding Detection) for example.
If we want to change the VMC BGP ASN number (65000 by default) we can do it by clicking “Edit Local ASN”.
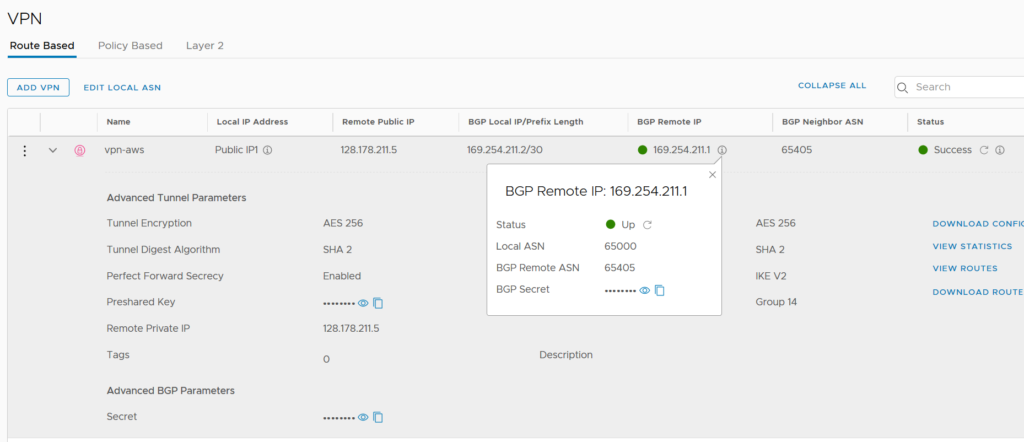
We are almost done for the VMC sid! 🙂
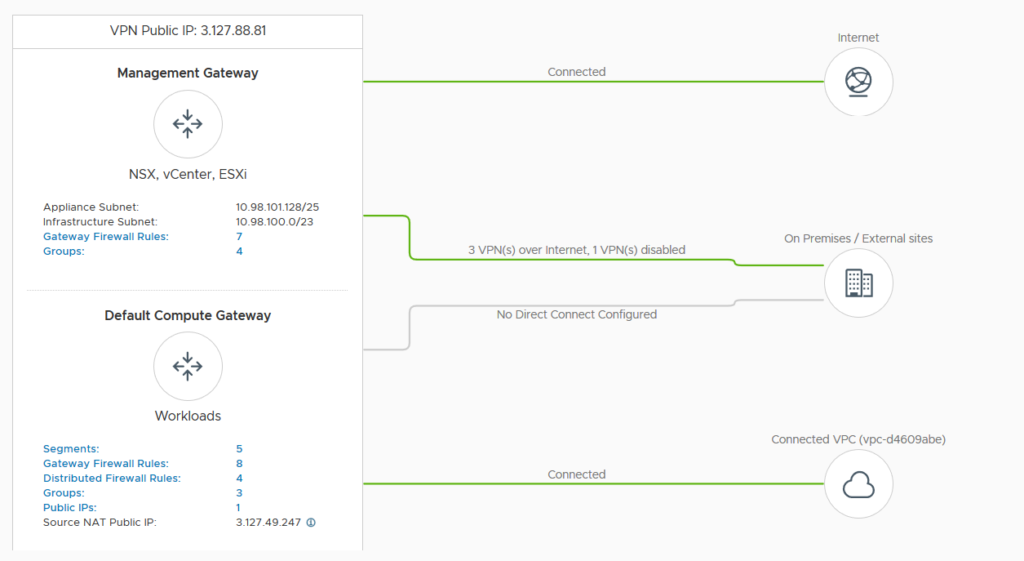
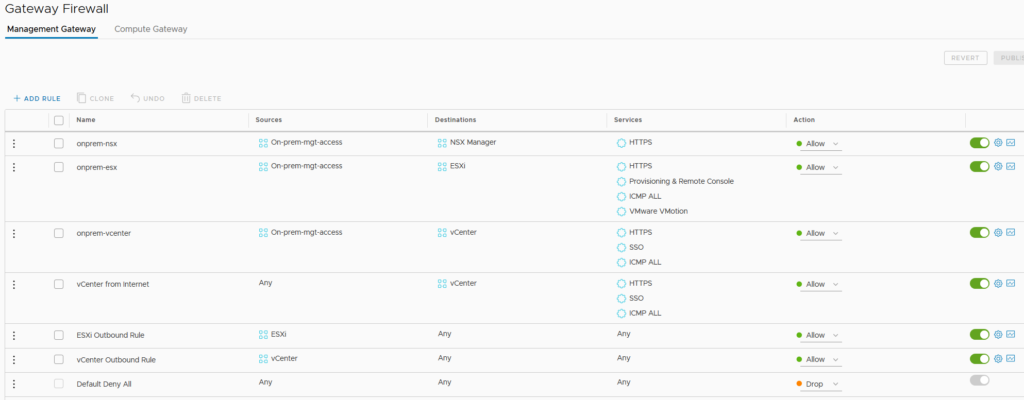
What we need now is to allow the traffic on the Gateway Firewalls.
There is one Gateway for each of the VMC sides (Management and Compute).
The easier way is to create a group on VMC in my case “On-prem-mgt-access” and add the IPs needed from on-premise side. Particularly the interface tunnel IP of the VPN on NSX-T
On the Management Gateway, we need to allow the access to the different appliances and hosts.
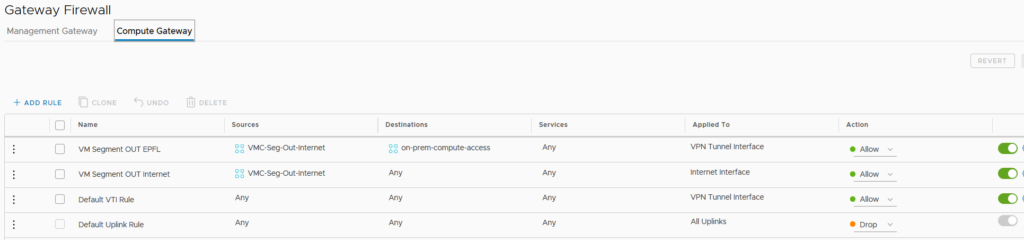
On the Compute Gateway, we need to allow all our VMC Segments to go outside the VMC Compute side.
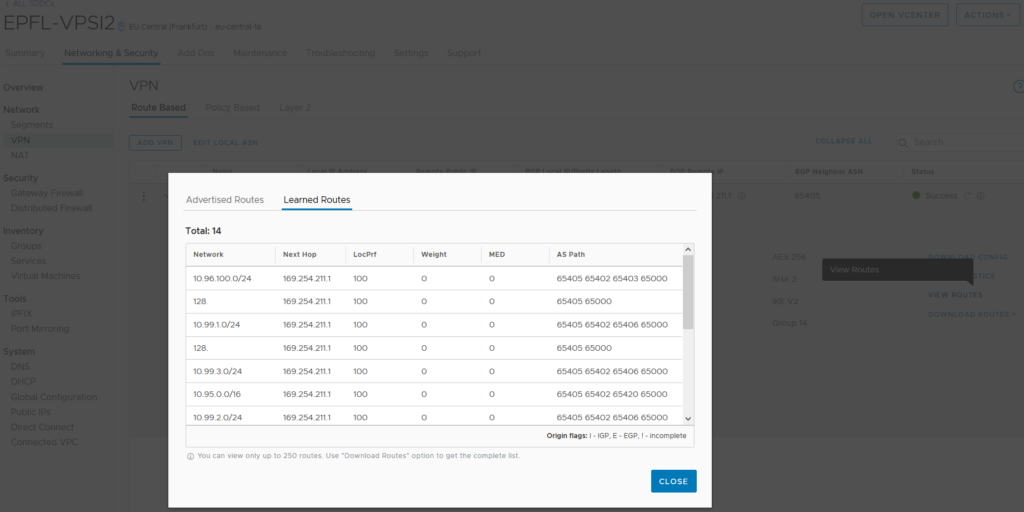
Once the VPN is set up correctly on both sides (NSX-T on-premise and VMC) with the firewall rules allowing the right traffic, we are able to see the routes learned through the tunnel via BGP.
It’s possible to disable the VPN from VMC side if needed.
Before we set up the VPN Tunnel, we were able to access the SDDC vCenter via his FQDN which was resolved with a public IP. We have to change this setting because the resolution address has now to be done with the private IP.