In these two parts, I will show and explain to you how to set UP and configure a connection beetwenn you NSX-T Datacenter on-premise and an SDDC on the cloud.
- Part 1: On-premise
- Part 2: VMware Cloud on AWS
- Part 3: Filtering BGP routes
Filtering BGP routes (On-Premise side)
Note: In these articles, I assumed people have already some knowledge about NSX-T components and are familiar with the NSX Manager UI, the edges and T0.
For privacy and security purpose, I will hide my on-premise public IP and the VMC public IP.
The version of NSX-T I used was 2.5.1 -> https://docs.vmware.com/en/VMware-NSX-T-Data-Center/2.5.1/rn/VMware-NSX-T-Data-Center-251-Release-Notes.html
I want to warmly thanks my VMware beast colleague Eric Krejci, the VMware NSX-T and VMC teams for their support.
At this point we have our IPsec VPN up and running! 🙂
Now, in my case and in many infrastructures, the default route 0.0.0.0/0 is forwarded in all our on-premise networks. Due to this, we have this default route in our on-premise T0 BGP routing table.
Meaning that this route will be send through the tunnel via BGP and all the VMC traffic, which is not on VMC side, will use the default route and use the Tunnel interface.
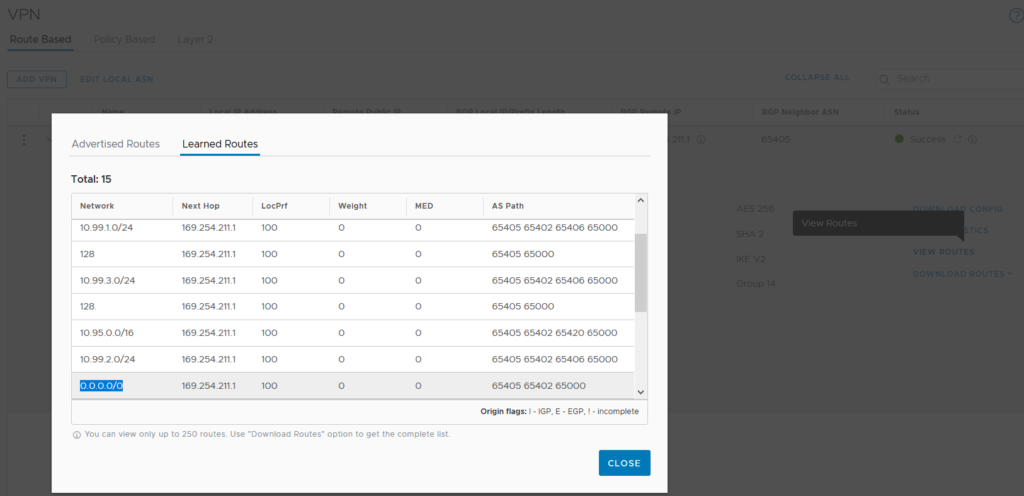
From VMC side you can see the learned routes from the IPsec VPN Tunnel under “VPN/Route Based/View Routes”. We can actually see that the default route is learned.
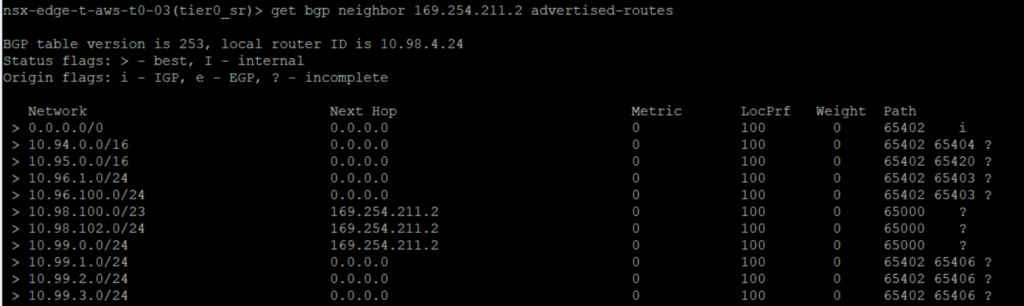
From on-premise NSX-T Datacenter side we have also the possibility to check which routes are advertised to the BGP neighbor. We can actually see that the default route is advertise.
We don’t want all the traffic to use the Tunnel because VMC as is own Public IP.
We want that the traffic which want to connect to “not on-premise networks” use this IP to reach directly the Internet.
We can reach this goal by using the IP Prefix List and Route Map filtering. I will explain this functionalities on this post.
IP Prefix List
An IP Prefix List allows you to filter routes in a routing protocol like BGP.
To create a new IP Prefix List on-premise side we can go to our T0 configuration page and under the Routing section click on the number of the IP Prefix Lists.
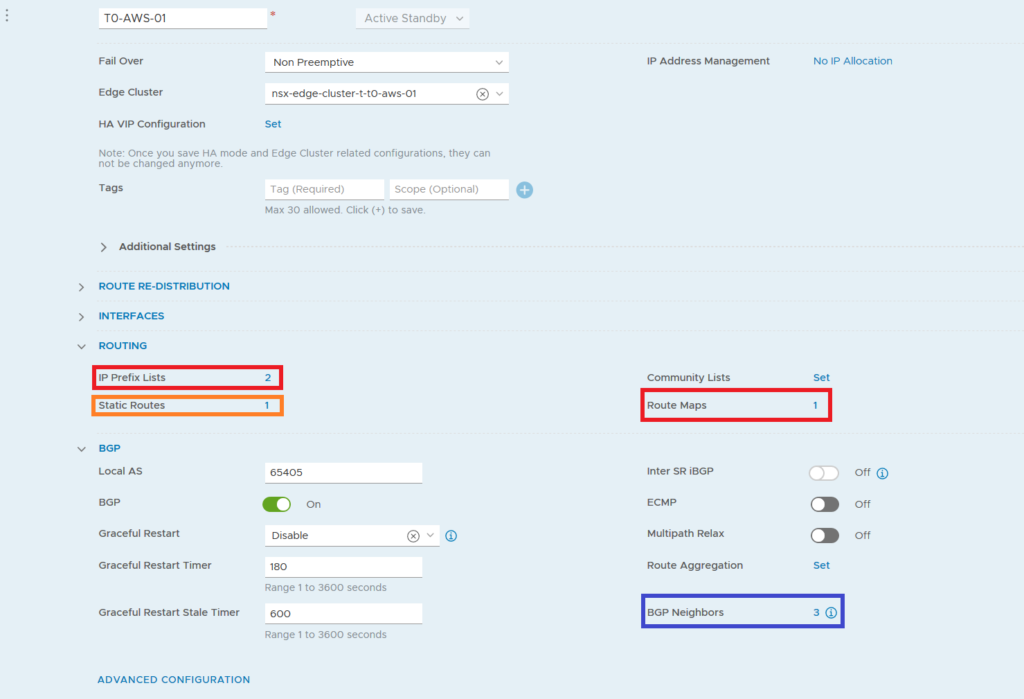
Here I’ve created a special IP Prefix List which includes the Prefixes to remove the default route but allow all the other routes.
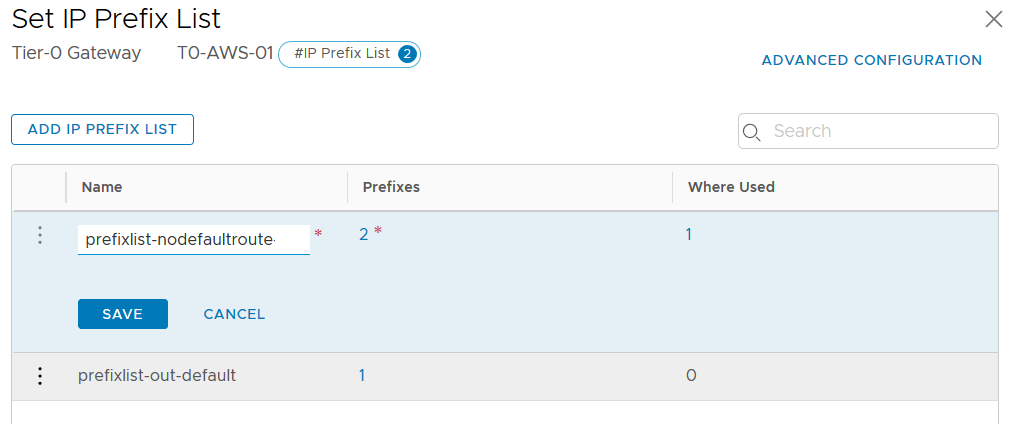
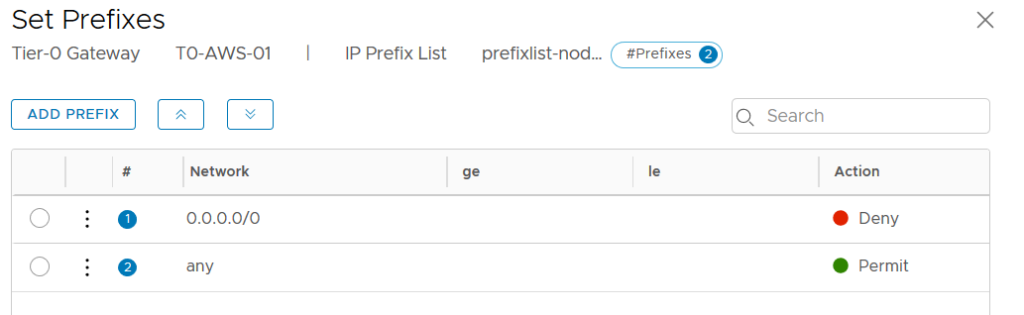
If we have more than one IP Prefix List, we can add these lists to a Route Map. And later on apply the Route Map instead of only one IP Prefix List.
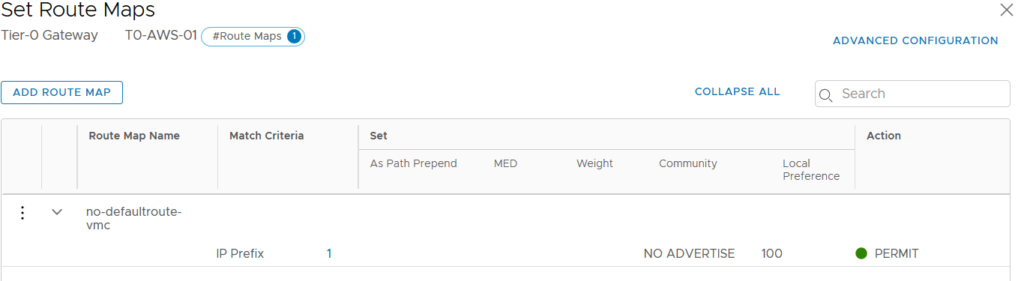
Now it’s time to apply this Route Map/IP Prefix List. It’s done at the BGP neighbor level and we have to specify if it’s an outgoing our ingoing filter. In our case we want to filter the BGP routes announced out through the VPN Tunnel.
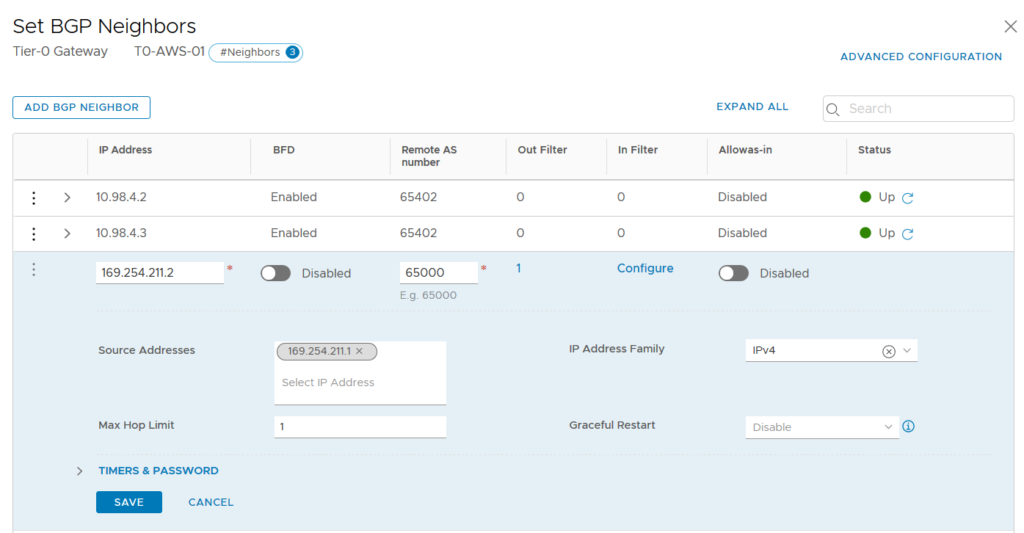
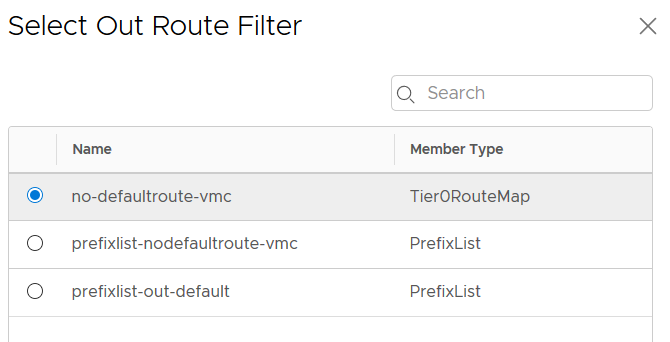
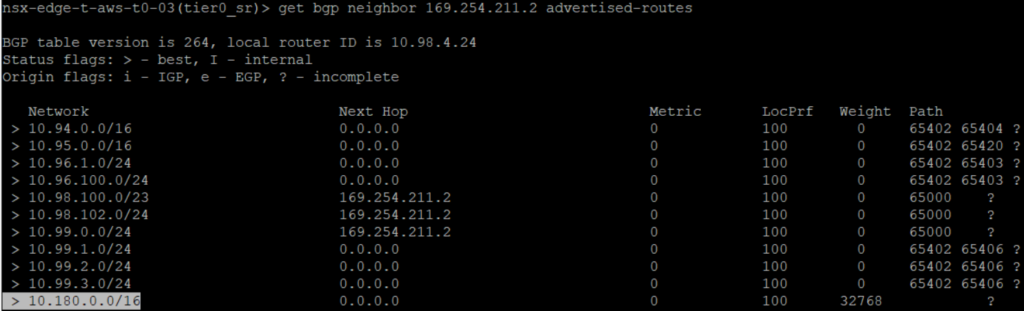
We can check that the default route is no more advertise to the BGP neighbor.
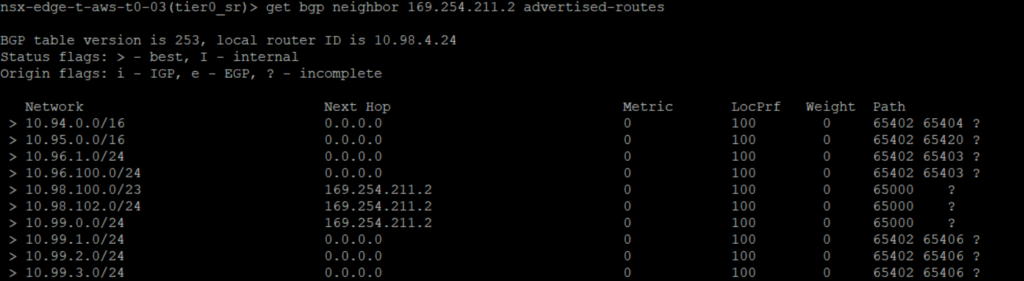
At this point VMs on VMC SDDC will now use the VMC public IP to reach the Internet!
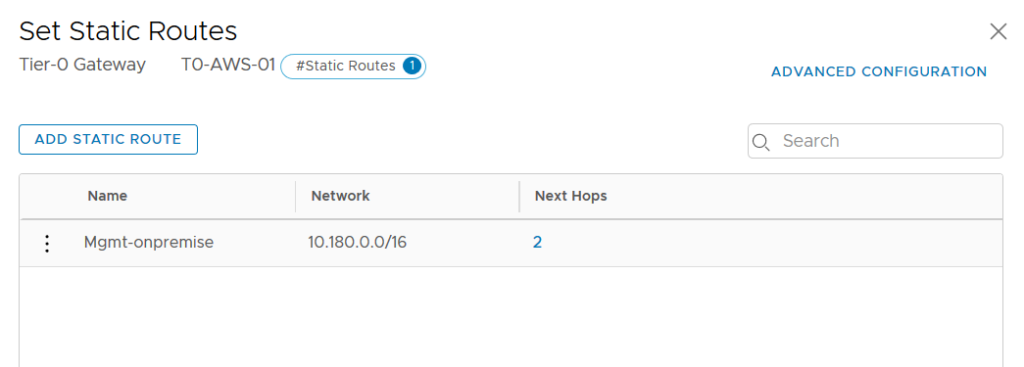
However, it’s possible that some on-premise networks were included on the default route 0.0.0.0/0. In my case, I need that the VMs on VMC use the VPN Tunnel to reach my Mgmt network on-premise 10.180.0.0/16.
We can do it by announcing on the T0 VPN a static route which will be propagate in the BGP advertised-route.
Set the Next Hops as the Router Ports which make the connection to your on-premise Network.
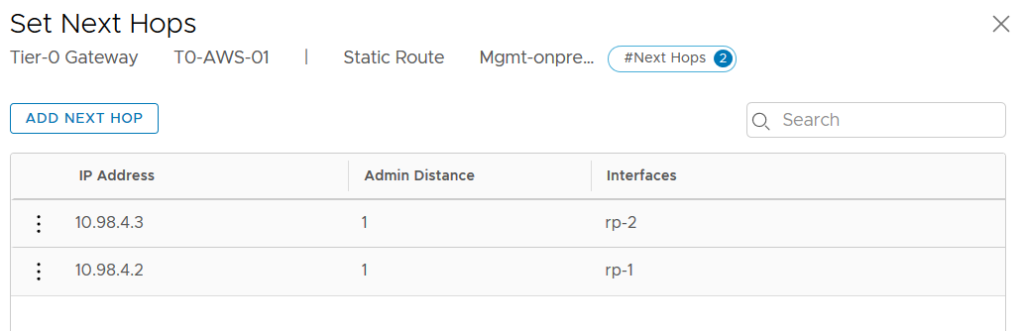
We can check that the newly added on-premise Network is advertise to the VMC BGP Neighbor.
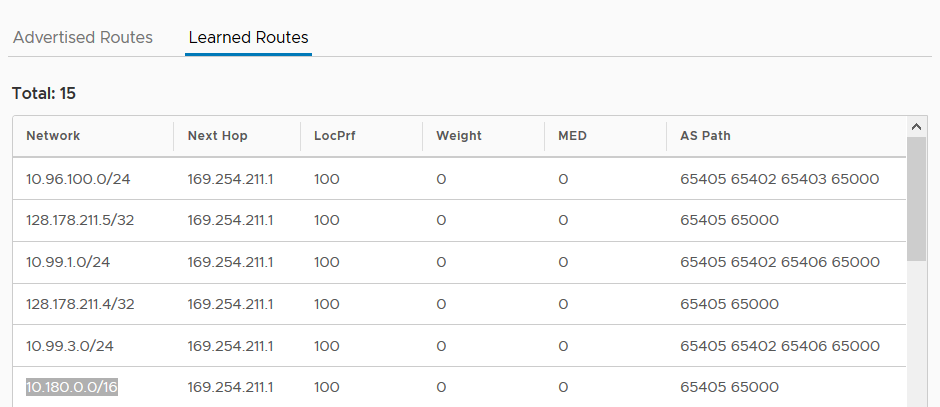
From the VMC side, we can also check that the on-premise side is correctly learned through the VPN Tunnel.
From a VM on VMC SDDC, we can now reach this on-premise network.